Identity Fusion Blog: IdentityManagement

Trust Is No Longer Binary
For years, organizations treated identity like a lock on a door. Authenticate the user, check the box, all’s good, move on. That model made sense when identities were mostly..

Analysts, Oracles, and the $80,000 Bake Sale
Walking out of the identity conference in Texas feels a bit like leaving a Renaissance fair where everyone forgot their costumes but kept the ticket prices. Vendors pulled me..

A 610 Billion Dollar Ponzi Scheme?
When I saw these headlines the first thing I did was look for a credible news source, I didn't find one. The rumor of a $610 billion AI Ponzi scheme didn’t surprise me; these..

Why You Must Start Planning for IAM 3.0 Today
There’s an old saying: “The best time to plant a tree was twenty years ago. The second best time is today.” When it comes to Identity and Access Management (IAM), we no longer..

Measure Twice, Cut Once
When I bought my first house some 30 years ago, I was young, ambitious, and wildly confident in my ability to take on home improvement projects I had no business tackling. It was..
The Myth Behind Modern IGA Deployments
Identity is no longer just a security layer—it’s now central to everything an organization does. From onboarding employees and enabling partner collaboration to powering seamless..

Why Typical Agile Falls Short in Large-Scale Identity, Access, and Governance Projects
It is easy to appreciate why Agile has become the default project management style for so many technology initiatives. Fast iterations, continuous feedback, and adaptable..
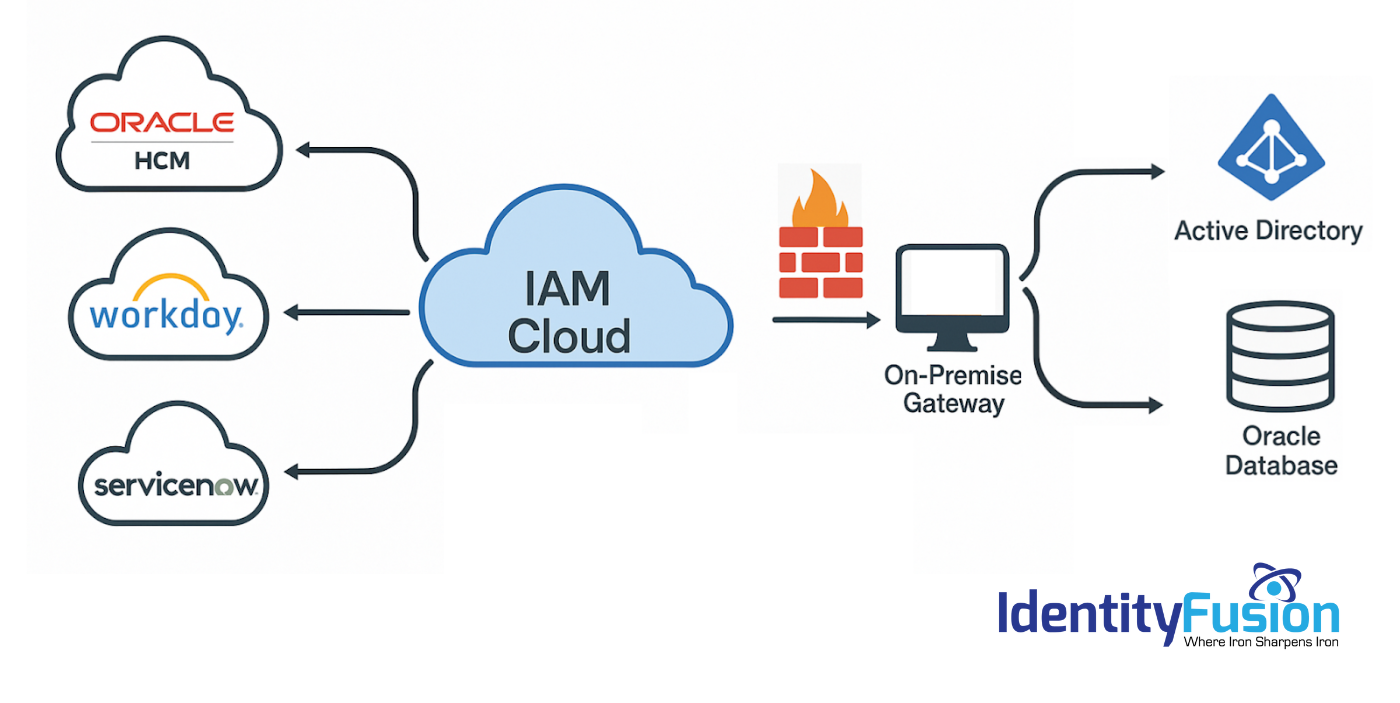
Migrating to an Identity Cloud: What the Vendors Won’t Tell You
As you explore the possibility of migrating your on-premise IAM solution to the cloud, you’ve likely heard promises of lower costs, simplified deployment, improved security, and..

The Emerging Future of Identity and Access Management: AI, Quantum Computing, and the Dawn of IAM 3.0
Part One of Two We all see that cyber threats are scaling faster than governance frameworks can adapt, the emergence of artificial intelligence (AI), machine learning (ML), and..
.png)
Identity Fusion Announces Strategic Partnership with Dock Labs to Bridge the Gap Between Legacy IAM and Next-Generation Identity Solutions
At Identity Fusion, our mission has always been to help organizations navigate the ever-evolving identity and access management (IAM) landscape with confidence and clarity. As..

Future-Proofing Identity: Bridging the Gap to Identity 3.0
Identity security is more critical now than it has ever been. Organizations have invested heavily in legacy identity implementations, including enterprise directory services,..

The State of Identity 3.0: Where Are We Now?
The evolution of digital identity is well underway, with Identity 3.0 bringing a decentralized, user-centric approach that could revolutionize how we verify ourselves online...
