Identity Fusion Blog: DecentralizedIdentity
Identity in the Age of AI: Why Governance Is the New Cybersecurity Imperative
In 2025, the stakes for Identity and Access Management (IAM) have never been higher. AI and machine learning are rewriting the rules of cybersecurity, and identity is at the..

The Emerging Future of Identity and Access Management: AI, Quantum Computing, and the Dawn of IAM 3.0
Part One of Two We all see that cyber threats are scaling faster than governance frameworks can adapt, the emergence of artificial intelligence (AI), machine learning (ML), and..
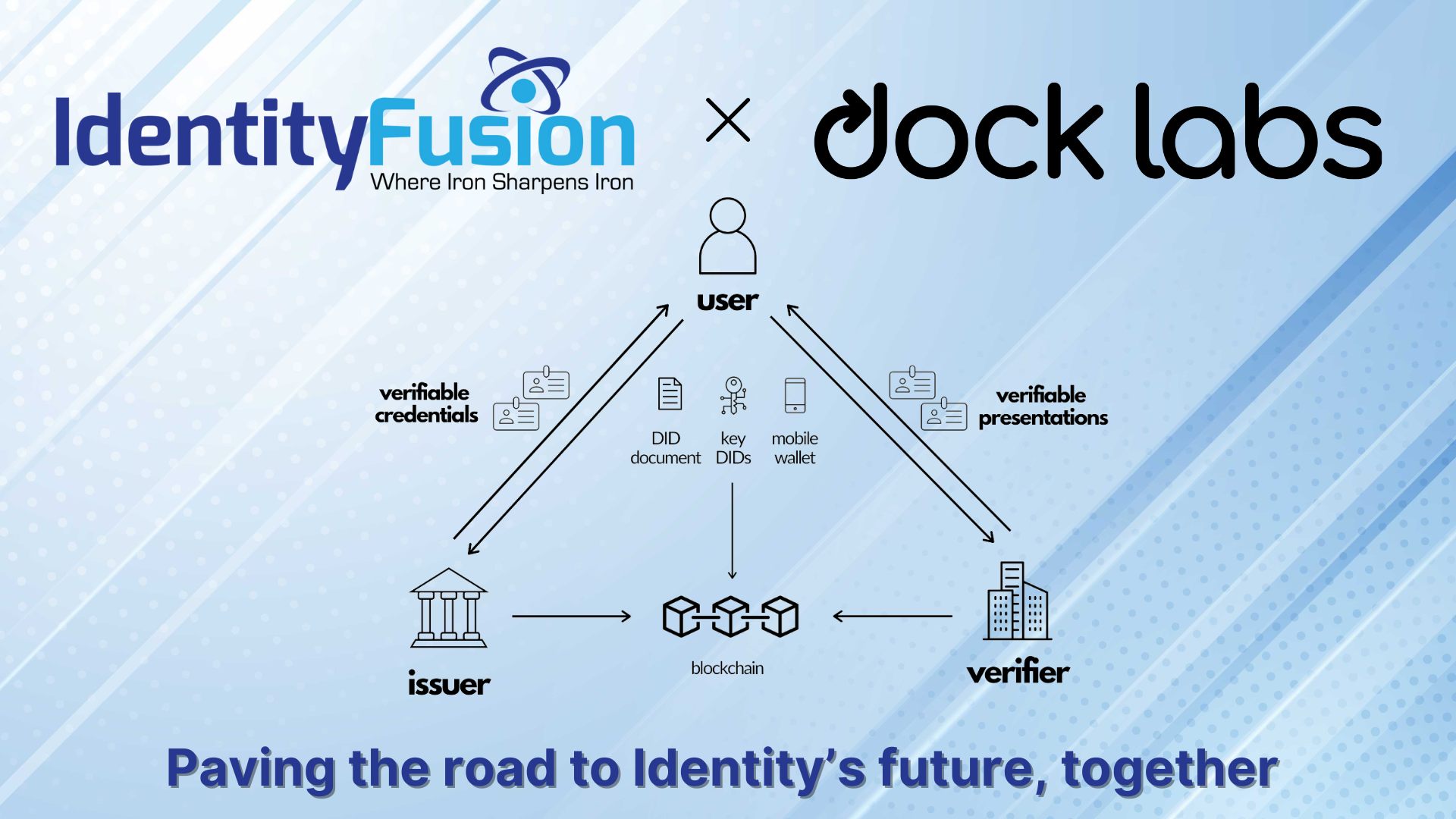
Identity Fusion Announces Strategic Partnership with Dock Labs to Bridge the Gap Between Legacy IAM and Next-Generation Identity Solutions
At Identity Fusion, our mission has always been to help organizations navigate the ever-evolving identity and access management (IAM) landscape with confidence and clarity. As..

Future-Proofing Identity: Bridging the Gap to Identity 3.0
Identity security is more critical now than it has ever been. Organizations have invested heavily in legacy identity implementations, including enterprise directory services,..

The State of Identity 3.0: Where Are We Now?
The evolution of digital identity is well underway, with Identity 3.0 bringing a decentralized, user-centric approach that could revolutionize how we verify ourselves online...

New Year, New Beginnings: Embracing the Future of Identity and Access Management in 2025
As the calendar turns to 2025, organizations are facing a rapidly evolving digital landscape. With increasing cyber threats, expanding digital ecosystems, and rising consumer..

Identity 2.0 vs Identity 3.0: A Comparative Analysis
As digital identity evolves, the limitations of traditional systems, often referred to as Identity 2.0, are becoming increasingly apparent. The rise of Identity 3.0 brings a..

The Road to Identity 3.0: Challenges Associated with Implementing a New Identity Paradigm
Imagine a world where you never have to worry about your identity being stolen, where proving who you are is as easy as a tap on your phone, and where you—not some corporation or..

The Ghost of Identity Yet to Come
In Dickens’ tale, the Ghost of Christmas Future offers a chilling vision of what may come, urging Ebenezer Scrooge to change his ways before it’s too late. The Ghost of Christmas..

The Ghost of Identity Present: Exploring Modern Identity Solutions
In A Christmas Carol, the Ghost of Christmas Present acts as both a guide and a mirror, revealing the current realities of Ebenezer Scrooge’s life. By showing him the joys,..

The Evolution of Identity: Past Lessons, Present Innovations, and Future Possibilities
Charles Dickens’ A Christmas Carol offers a timeless narrative of reflection, transformation, and hope through its depiction of the Ghosts of Christmas Past, Present, and Future...

Welcome to Identity 3.0: A Revolution in Digital Identity
The way we manage digital identity is under siege. Traditional identity and access management (IAM) solutions, often built around centralized databases and opaque processes, have..
