As digital identity evolves, the limitations of traditional systems, often referred to as Identity 2.0, are becoming increasingly apparent. The rise of Identity 3.0 brings a transformative approach that addresses these shortcomings with a focus on user empowerment, privacy, and security. Let’s explore how these two paradigms compare and why Identity 3.0 is poised to revolutionize identity management.

Key Technologies
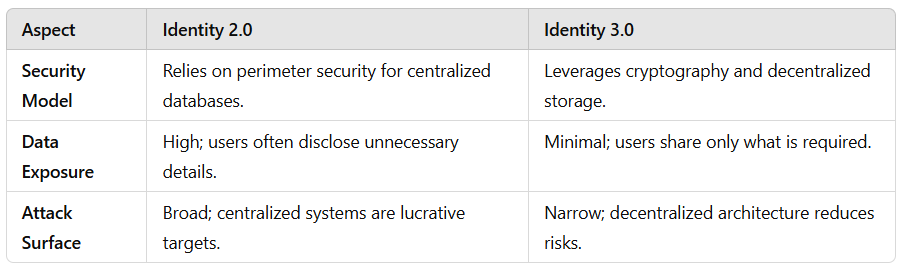
Identity 2.0: Centralized and Vulnerable
Identity 2.0 systems rely on centralized databases and intermediaries to manage digital identities. Examples include:
- Social Login Systems: Using accounts from Google, Facebook, or Apple for authentication.
- Username and Password: A widespread but outdated method prone to breaches.
- Identity Federations: Systems like SAML or OAuth that enable limited interoperability but still centralize control.
These systems are inherently vulnerable to:
- Data Breaches: Hackers target centralized data repositories, leading to massive leaks.
- Over-collection of Data: Organizations collect more personal information than needed, increasing privacy risks.
- Fraud: Phishing and credential stuffing attacks exploit weak password systems.
Identity 3.0: Decentralized and User-Centric
Identity 3.0 introduces technologies that eliminate the need for central authorities and reduce attack vectors:
- Verifiable Credentials (VCs): Digital, cryptographically signed credentials that users can store and share securely.
- Decentralized Identifiers (DIDs): Unique, user-controlled identifiers that are not tied to a single authority.
- Digital Wallets: Secure apps that manage credentials and enable selective sharing of data.
- Blockchain/DLT: Provides a tamper-proof mechanism for verifying credentials without a central authority.
User Experience
Identity 2.0: Fragmented and Inefficient
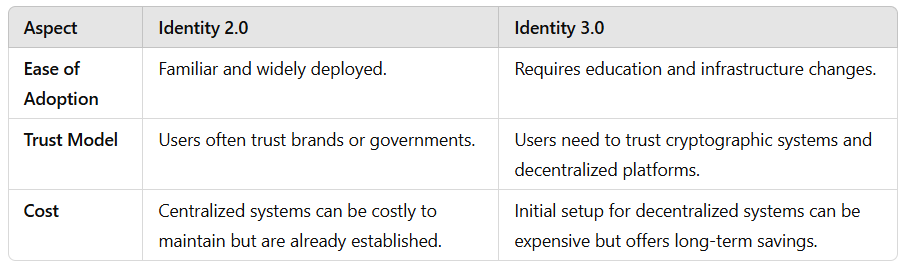
Users often juggle multiple accounts and passwords across different platforms. The reliance on third-party logins creates dependencies on major corporations, limiting user control and creating single points of failure.
Identity 3.0: Unified and Empowering
Identity 3.0 simplifies the user experience by:
- Allowing users to store all credentials in a single digital wallet.
- Enabling instant verification without intermediaries.
- Eliminating the need to remember passwords for every service.
For example, proving your age under Identity 2.0 might involve showing a physical ID with your full name, address, and birthdate. Under Identity 3.0, a digital wallet could verify your age without revealing any additional information.
Adoption Challenges
The Future of Identity
Identity 2.0: Legacy Systems on Borrowed Time
While Identity 2.0 systems are deeply entrenched, their vulnerabilities and inefficiencies are becoming unsustainable. The reliance on centralized control and lack of privacy safeguards make them ill-suited for the demands of modern digital ecosystems.
Identity 3.0: A New Era
Identity 3.0 offers a vision of the future where users are in control:
- Improved Security: Reducing dependency on centralized systems makes breaches less catastrophic.
- Enhanced Privacy: Selective disclosure ensures users only share what’s necessary.
- Global Interoperability: Open standards enable seamless identity verification across platforms and borders.
Conclusion
The transition from Identity 2.0 to Identity 3.0 is not just a technological upgrade—it’s a philosophical shift. While Identity 2.0 systems served as the foundation of the digital identity landscape, their limitations are driving the need for a decentralized, user-first approach. Identity 3.0 stands ready to meet the challenges of an increasingly connected and privacy-conscious world, offering a secure, efficient, and empowering future for digital identity management.
The question is no longer if we’ll move to Identity 3.0 but how quickly we can embrace this essential transformation.
Additional Articles in this Series
Welcome to Identity 3.0: A Revolution in Digital Identity
The Road to Identity 3.0: Challenges Associated with Implementing a New Identity Paradigm
The State of Identity 3.0: Where Are We Now?
Future-Proofing Identity: Bridging the Gap to Identity 3.0

